-
Using
- Importing Services & APIs
- Comparison to alternatives
- OpenAPI Mocking and Testing
- Swagger Mocking and Testing
- AsyncAPI Mocking and Testing
- Postman usage for Microcks
- gRPC Mocking and Testing
- GraphQL Mocking and Testing
- SoapUI Mocking and Testing
- Http Archive usage for Microcks
- Using exposed mocks
- Getting direct API
- Testing with Microcks
- Advanced topics
- Organizing repository
- Templating mock responses
- Dispatcher & dispatching rules
- Microcks APIMetadata
- Monitoring & Observability
- Installing
- Automating
- Administrating
- Guides
External Secrets
🗓️ Last updated on November 19, 2019 | 2 | Improve this pageIntroduction
Starting with Microcks version 0.7.0, we add the ability to manage some forms of Secrets in order to access private HTTP(S) repositories su as Git ones.
Secrets can only be managed by Microcks administrator - we mean people having the administrator role assigned. If you need further information on how to manage users and roles, please check here
. Secrets management is simply a thumbnail with the Administration page that is available from the vertical menu on the left once logged in as administrator.
Authentication secrets
Secrets are displayed in a list and simply classified using a name and a description. You may use this screen to create, edit or delete secrets. Secrets are then bound to usages - today, only import jobs are using secrets.
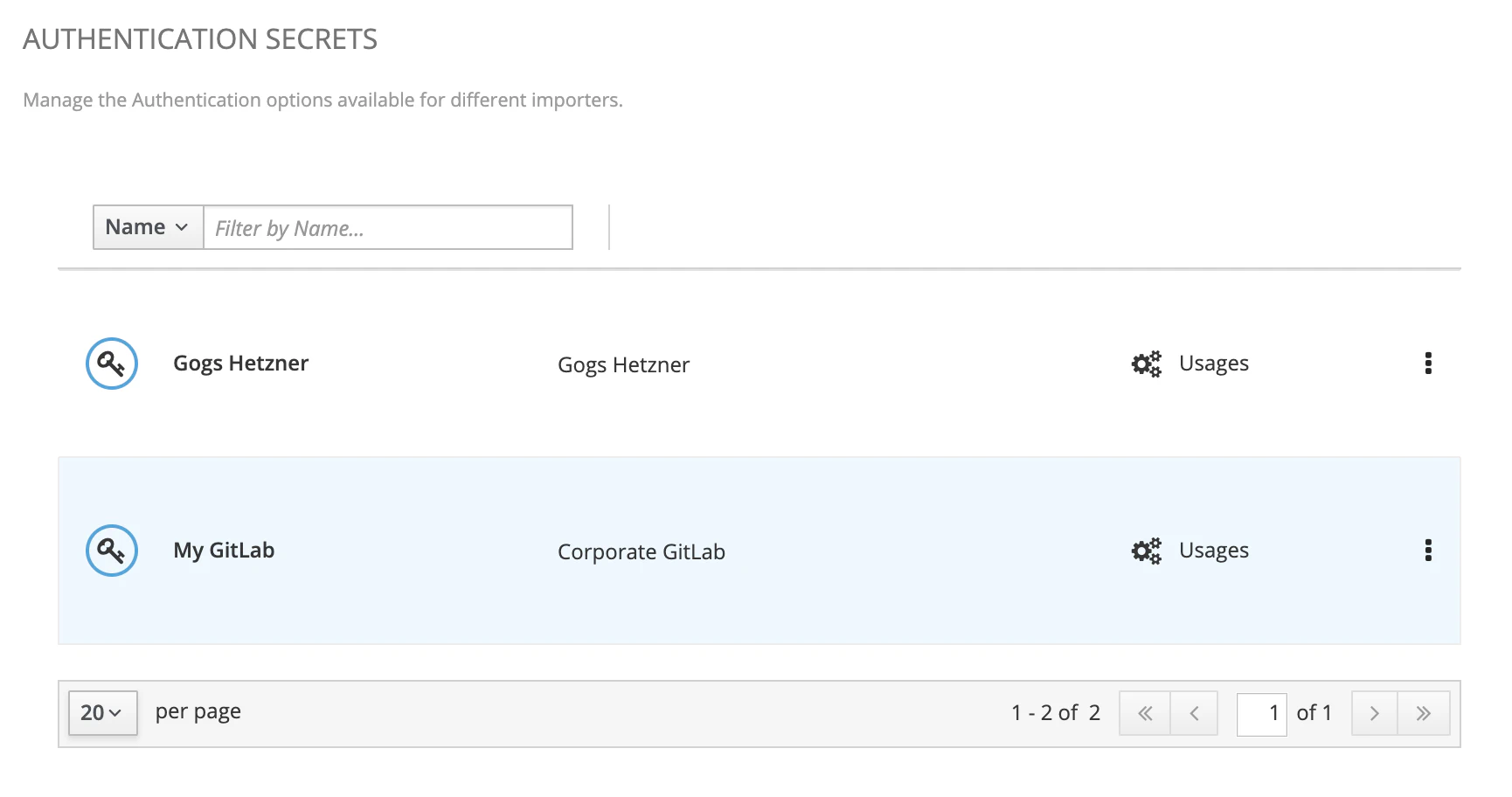
Let see how to create/update a secret and its properties below.
Secret properties
Now imagine I want to create a secret that will hold informations on how to access my corporate GitLab instance. Here’s the form you’ll have to fill below. It may imply authentication method and properties as well as transport encryption information such as the custom certificate to use.
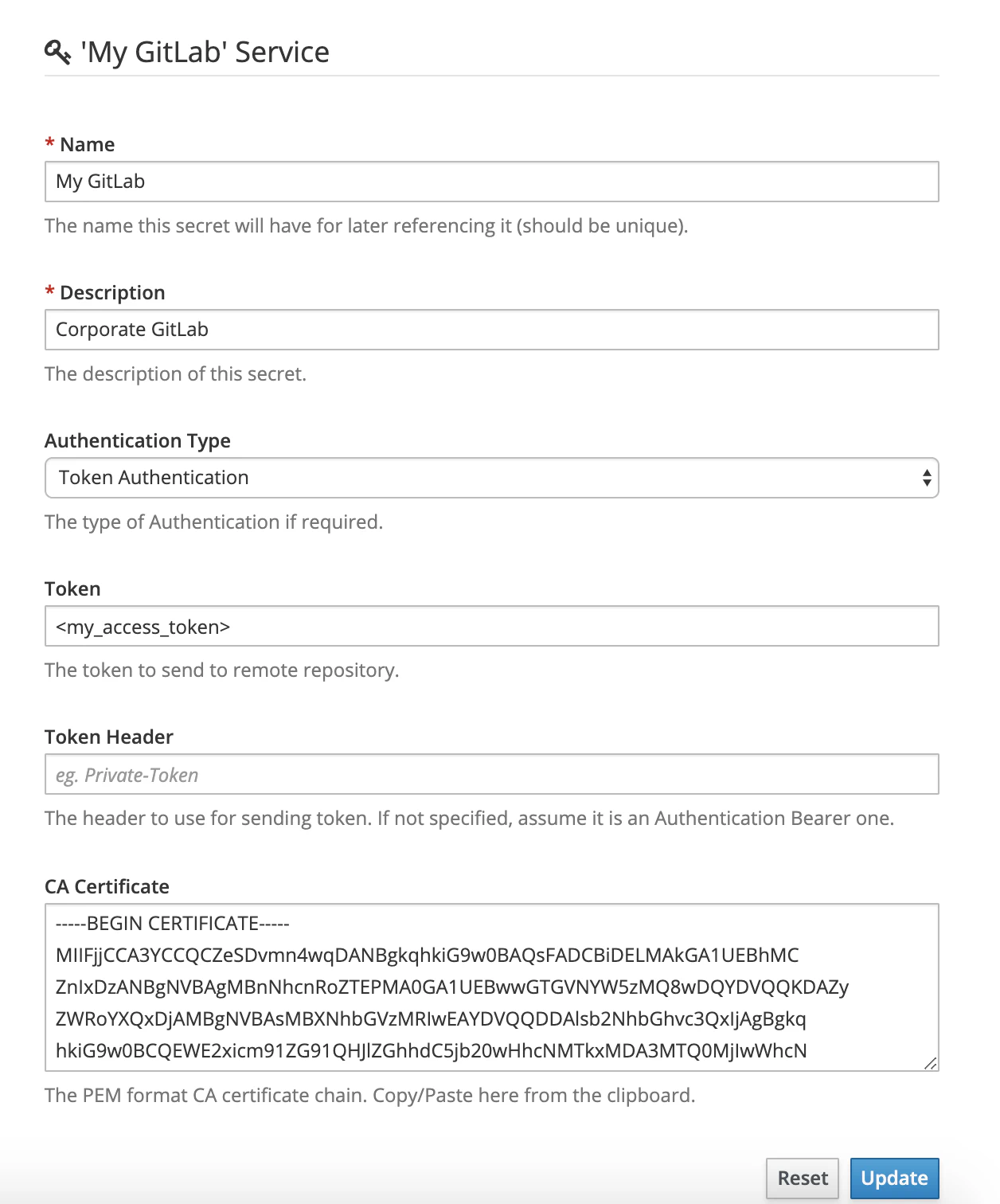
Authentication may be realized using different methods described below.
| Authentication Type | Description |
|---|---|
None |
No authentication is actually realized. In this case, the secret may only be useful to hold custom certificate to access private resource. |
Basic Authentication |
An HTTP Basic authentication is attempted when connecting to remote resource. When selecting this method, form will just ask for a User and a Password. |
Token Authentication |
An HTTP Bearer or custtom authentication is attempted with the prvided Token. If no Token-Header is specified, the standard Authentication: Bearer <provided token> is attempter. If a Token-Header is specified, token is added as the value of this specific header. |
The CA Certificate is just here to gather a custom certificate or certifcate chain specified in PEM format.
Adding secret to an import job
Now that you have created and managed a secret, you can add it to your Import Job. For doing that, just go and update a job: the second step of the wizard modal is dedicated to security concerns. You may now just add a reference to (thus a usage of) one of your secret.
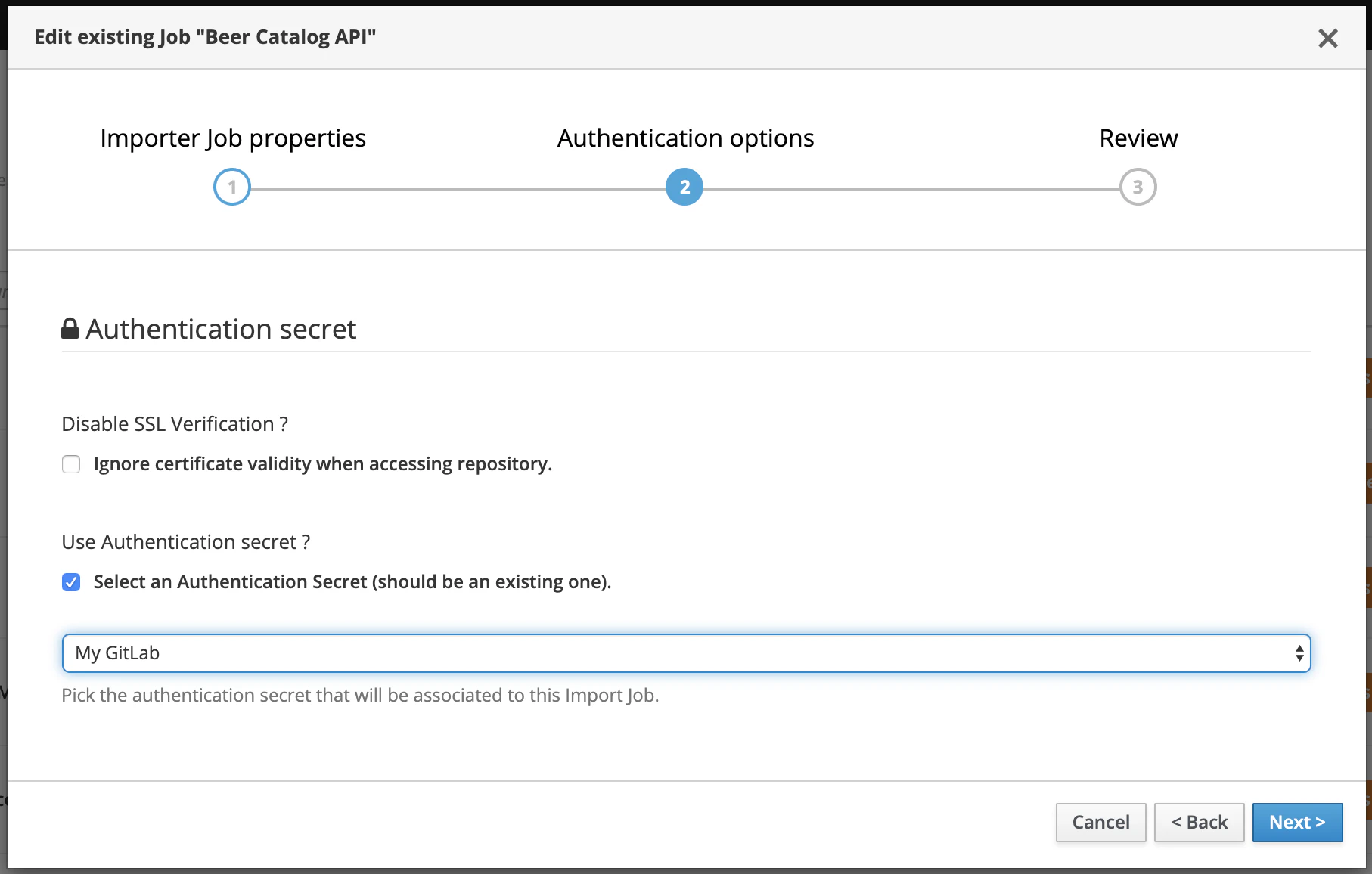
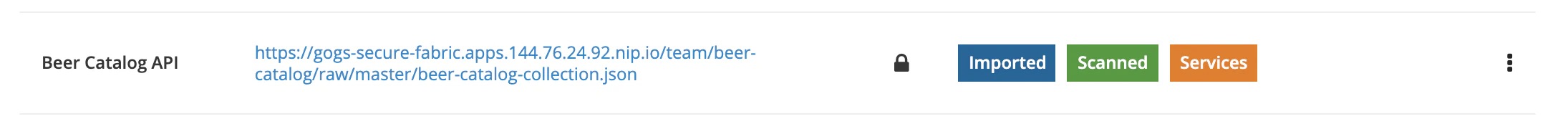
When Microcks will scheduled and execute this job to check update of artifact resource, it will simply used the referenced secret. Now your job is identifier as using a secret on the UI:

Still Didn’t Find Your Answer?
Join our community and get the help you need. Engage with other members, ask questions, and share knowledge to resolve your queries and expand your understanding.
Join the community